2015-12-05 »
"""We have a computer that is potentially catawampus,” Lieutenant White said.
“What does catawampus mean?” said Major Burley, the co-pilot, with a laugh.
“Cray-cray,” she responded.
"""

2015-12-06 »
From my reading on the plane:
"""
...these are not acts of sadism. They are acts of group survival. They function, oddly enough, to spur future society members to find the group more attractive and worthwhile. As long as it is the case that people like and believe in what they have struggled to get, these groups will continue to arrange effortful and troublesome initiation rites. The loyalty and dedication of those who emerge will increase to a great degree the chances of group cohesiveness and survival.
"""
– Robert Cialdini, on Google's interviewing and promo processes
2015-12-11 »
At first I thought my agent had finally come through, but no, not the email I thought it was.

2015-12-17 »
Hey, cool. The contractors came through, and I can now steer wifi clients between access points on command. We don't yet have a "brain" program that will actually send the actual commands, but I figure... how hard can it be, right??
In other news, Android L and later are supposed to have improved background scanning so that when you kick them off your AP for steering purposes, they can join another AP very fast (because they've already been surveying the environment in the background). That seems true! My near-dead-with-bloat 2012 Nexus 7 with Android L (NEVER EVER DO THAT) transitions in tens of milliseconds without a glitch. The future of wifi might actually be bright.
2015-12-18 »
I love isoping because it can tell me which direction my packet loss is in:
35.9 ms tx 35.2 ms rx (min=34.8) loss: 19/183 tx 0/183 rx
I dislike FiOS because that's not even a slightly reasonable level of packet loss.
(Yes, I tested the same remote host from a non-FiOS connection. No loss.)
2015-12-19 »
This is a bit simplistic but an interesting point. Note that it should be able to disassociate any camera within wifi scanning range, not just on your own network.
http://julianoliver.com/output/log_2015-12-18_14-39
Naturally, you probably shouldn't be screwing up other people's cameras. And there's an 802.11 extension for signed management frames which would disable this particular variant of the attack if everyone used it (ha ha) (although of course channel-wide jammers and other more aggressive attacks would still work).
Given that wifi is almost impossibly attractive as a deployment platform for spy cams, I wonder what the long-term response to this will be. My guess: stealth-mode cams that store-and-forward or otherwise disguise their traffic patterns to not look like cams. (The code linked here just kills based on MAC OUI, but there's no reason the technique won't stop there.)
2015-12-20 »
Last week I asked an RF Engineer candidate how to optimize a too-dense wifi environment with hidden nodes and excellent signal propagation. I regret nothing. (The interview went well, but no silver bullets, I'm afraid :))
2015-12-27 »
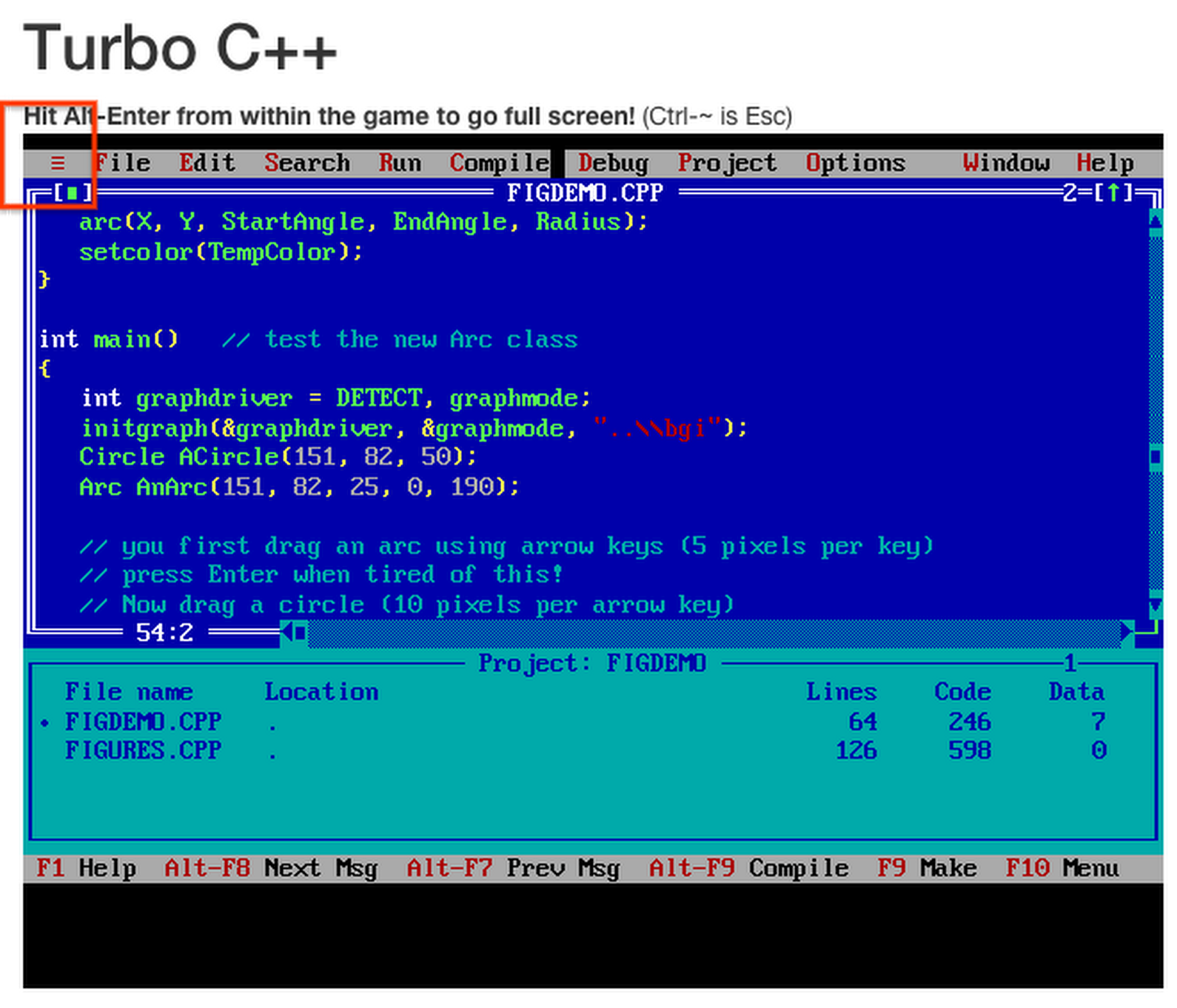
Holy moley, it's the hamburger menu, circa 1990. I spent untold hours of my youth in this program; I can't believe I didn't remember it.
In other news, this naclbox thing is pretty neat. http://www.naclbox.com/gallery/turboc
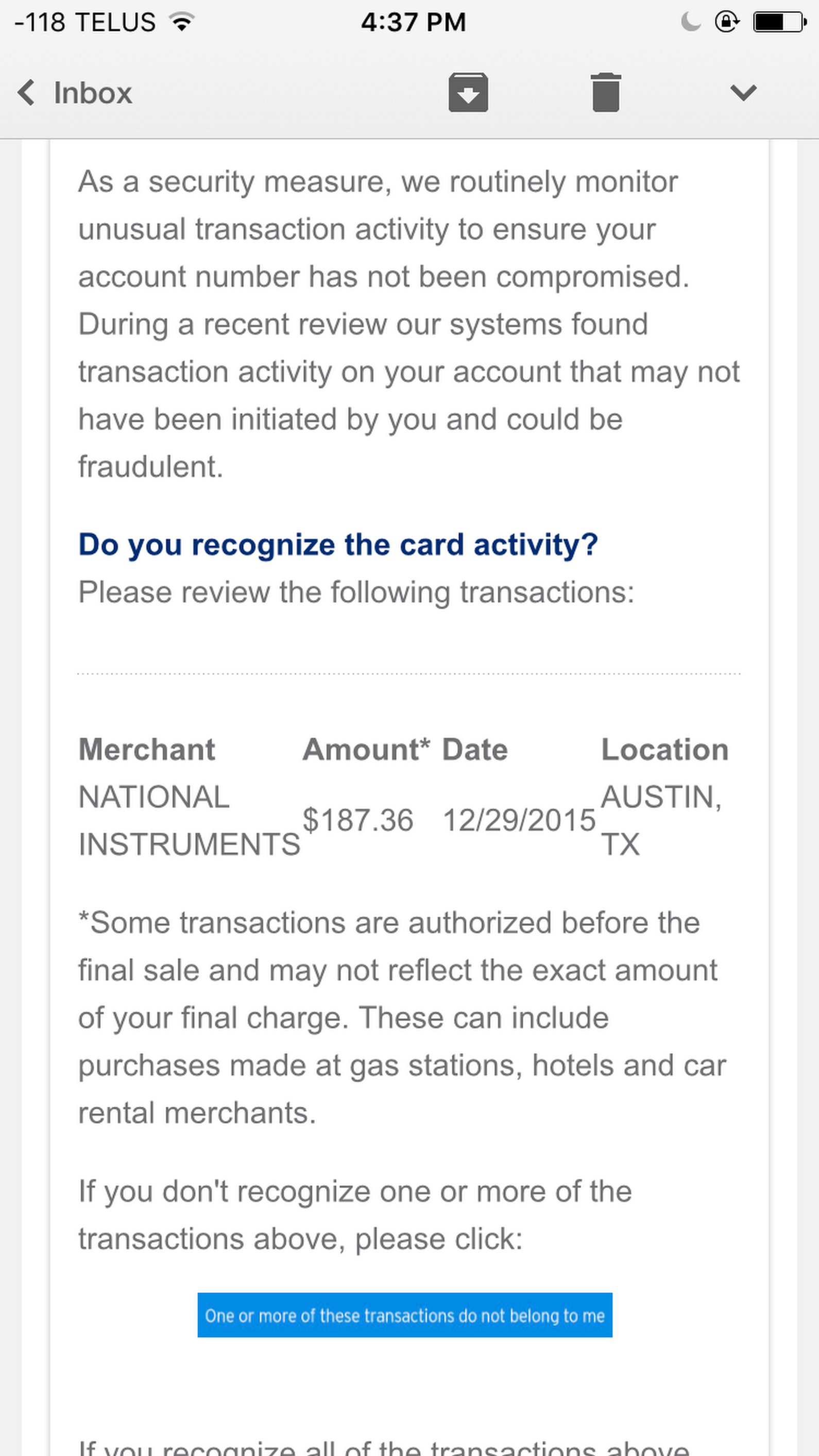
2015-12-29 »
Okay, fraud detector, you have a point. I bet tons of fraudsters buy equipment from National Instruments over the holidays.
Why would you follow me on twitter? Use RSS.
